
A no-bull technical guide to EV HTTPS
You deserve a better explanation of EV than a CA yelling 'trust' at you.
July 12, 2021
We went to EdgeConf last Saturday. Edge is an invite-only conference for the developers of all the major browsers, standards bodies, authors of common web libraries, and developer relations people from every major web standards organization.
The Chrome team, the Microsoft folks, Mozilla staff, W3C representatives, people from GSM-A, folk from ECMA-262, and the CDNs were there. Edge was a great event and a great deal already seems to be happening already from some of the discussions at that event.

Not everyone involved in the web had a presence at EdgeConf. Out of the hundreds of CAs your OS trusts, zero attended. There only groups in the room involved in issuing certificates were CertSimple and LetsEncrypt.
Listening to web developers and their experiences during both the Security Panel Session and the following Security Breakout there were a number of fairly understandable misconceptions around certificate validation.
This is symptomatic of the current relationship between CAs and developers:
Developers have a lot of questions and want specific, technical answers. CAs yell 'Green bar! Trust!' repeatedly and try and sell them IE5 support or extra visitors by users with browser extensions. This does little to ensure developer confidence in Certificate Authorities or justify the significant price difference between EV certificates and cheap/free DV certificates beyond what the browser displays.
The CA/Browser Forum, a group of all the major CAs and browser makers that create the EV standard, has a tiny official FAQ that omits answers to most of the common questions. You could read the EV spec, comprising the Baseline requirements and EV requirements, but like any spec, they're long, detailed, and some parts of it - like site inspections looking for permanent signage, or steps only relevant for government-departments applying for EV certs - are extremely unlikely to occur in a normal EV process.
The result is that developers often have little insight into the processes behind either DV or EV HTTPS validation.

We're biased: CertSimple only sell EV certificates. Everything you're about to read is referenced in the EV guidelines or baseline requirements.
What are DV and EV HTTPS?
DV and EV HTTPS are different levels of validations - identity checking - used for SSL certificates.
In the 90s, Certificate Authorities required applicants to go through a long processes of faxing documents back and forth to prove their identity, prior to being issued an SSL certificate.
Over time, one CA dropped the identity checks in favor of having an official-sounding admin address at a domain. The other CAs soon followed suit.
DV (Domain Validation) is the name given retroactively to the most common kind of SSL certificates, where proof of control over a domain is used to issue a certificate for that domain.
EV (Extended Validation) is a newer validation standard requiring proof of the company's identity in addition to control over the domain. Browsers users typically see EV as a green bar with a company name in their address bar.
Who decides what DV and EV are?
Browser makers and Certificate Authorities, via the CA/Browser forum
Where is the EV spec so I can read it?
Additional requirements of extended validation are stored in the Extended Validation requirements
All certificates (both EV and domain validated) should follow the Baseline Requirements but since DV certificates existed before the requirements this is not guaranteed.
EV certificates must follow the EV guidelines (which extend the baseline requirements).
Do EV certs have better encryption?
No. All encryption algorithms are available for both types of certificate. Security is considered to have three elements:
- Confidentiality
- Integrity
- Authentication
The confidentiality and integrity of EV certificates is the same as DV certificates.
Do EV certs have better security?
Yes. The authentication requirements for an EV certificate are higher. EV certificates prove a real-world company: DV certificates prove you own a domain which may or may not represent a real world company.
This is why EV certificates have a different subject from DV certificates.
What is a certificate subject?
It's the thing being attested to by the certificate. In DV's case the subject is a domain, in EV's case it's a legal entity, typically a company but sometimes a registered charity or other legal entity.
Show me.
Here is a DV cert:
openssl x509 -in domain-validated-example.com.crt -noout -text | grep Subject
OU=Domain Control Validated
CN=example.com
DNS:example.com
Here is an EV cert:
openssl x509 -in extended-validated-example.com.crt -noout -text | grep Subject:
jurisdictionOfIncorporationCountryName=GB
businessCategory=Private Organization
serialNumber=09378892
C=GB
ST=City of London
L=London
O=example Limited
CN=example.com
DNS:example.com -
Companies in the UK are registered with a UK-wide organization called Companies House. The serialNumber 09378892 in the certificate above is a company registration number from Companies House.
In the USA, organisations are registered on a per-state basis, so serialNumbers in US certificates refer to a company ID at the relevant Secretary of State.
What do I have to do to get a Domain Validated cert?
Have a domain - any domain will do. Typically, one of:
- Receive email at an official (admin@domain.com, postmaster@domain.com) looking email address for a domain
- Receive email at an email address mentioned in
whoisfor a domain - The ability to publish a DNS TXT record for a domain
- Shell access to a machine (for nonce based systems) that has a DNS A record at a domain
The most common method used is 'official looking email address'. The domain can look like another company, but that's not checked. All a DV cert asserts is that you have a domain, not whether the domain represents a particular legal entity.
What does a Domain Validated cert mean for an end user?
DV gives you a lock when you connect to https://bank.com/onlinebanking - since you are genuinely communicating via an encrypted channel to bank.com.
DV would additionally give you a green lock when you connect to https://bank.com-onlinebanking.ru, a site that looks similar to bank.com but which is in Russia. The 'origin' in this case is com-onlinebanking.ru. However - since you are communicating via an encrypted channel to com-onlinebanking.ru, the lock displays for https://bank.com-onlinebanking.ru exactly as it would for https://bank.com.
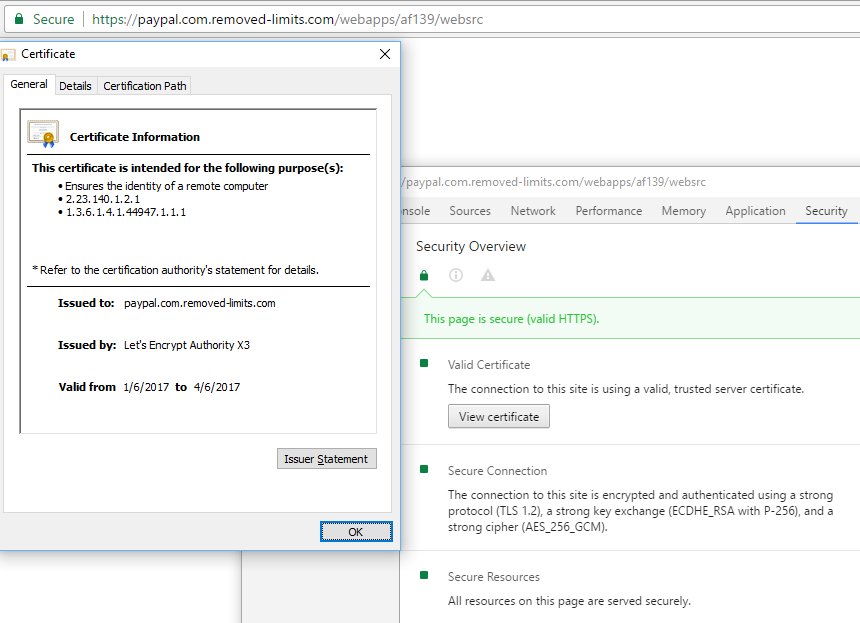
This can and has happened before with some of the largest sites on the internet.
There are a few problems here:
- An 'official looking' email address may not be sufficient proof of a link to the domain.
- Users are interested in whether they're connecting to their bank. The origin https://bank.com or https://bank.com.onlinebanking.ru or https://bank.com.mg may not be sufficient to answer that.
- Wildcard certificates make it possible for certificates to be used for domain names that appear to look like other companies.
- There is no way to know the domain is under the control of the company the user thinks it is.
Why do companies get EV certs?
For the same reasons you'd want to prove your real worl identity online, including:
- To prevent phishing attacks on their staff or customers
- To prove to potential customers they're sending data to a verified real world company, rather than a random website
- To distinguish that they represent a company, whereas affiliates and similar sites do not
What do I have to do to get an Extended Validation cert?
Extended validation checks:
The company exists at a 'Qualified Government Information Source', is active, and has a verifiable physical address
In the UK: Companies House, in Israel, the Ministry of Justice, in the US, the local Secretary of State.
The company exists at an Qualified Independent Information Source, and when contacted, someone will confirm the admin contact's authority in the company.
Typically, Dun & Bradstreet, Hoovers, White Pages, etc. These can't be self reported: the Qualified Independent Information Source must review the information.
These contact details will be used to contact the company by telephone. A verifying agent from the CA will ask to speak to HR for larger companies. Then the verifying agent will confirm the authority of the admin contact to make decisions on behalf of the company (e.g., get a certificate issued), and speak to the admin contact to make sure they approve of the order. This is designed to stop someone who works for the company from creating their own rogue certificates.
All the domains applied for were visually inspected by the CA
EV requires all the domain names must be in the certificate, and inspected by the CA. If you request a certificate for bankofamerica.com-othercompany.ru you'll be rejected.
There are no wildcards, but you can have as many domain names as you want. You can also add domain names to a certificate later.
The company controls the domains
Per the Baseline Requirements, applied to all certificates. These steps are the same as the steps for DV certificates specified above.
Other steps
Some CAs typically ask an lawyer or accountant to write a letter of attestation, which allows the lawyer/accountant to attest to some aspects of the company, and the CA to do less work. The CA still has to check the lawyer/accountants credentials.
What does the EV process look like?
Here's an EV order running from start to finish. Note CertSimple checks your detais before you pay, so CertSimple is a lot faster than other CAs.
Should I trust CAs?
No. Thankfully Chrome requires all EV certs issued post January 1 2015 to have certificate transparency. This can be used to stop a CA from issuing certificates for your organisation using someone else's key pair.
Since Chrome has a large market share, this effectively means that all EV certificates must now support Certificate Transparency.
Are the details you supply to the CA used to validate your certificate?
No.
One person at Edge conference thought the EV process seemed too easy. There's a very common, very understandable misconception that we've even had to clarify in our own communication:
Yes, the EV application process asks you for the phone number of a administrative contact. This is not actually used to validate your identity. Here's are common conversations we have with admin contacts:
-
"You're asking for a Doing Business As name (trading name in the UK) to appear on your EV cert. Can you provide evidence of that name being registered with the government?"
-
"We've investigated your company and the State of California says you're suspended because you missed a bill. We can't issue your certificate until this is resolved."
PS. CertSimple now check that companies are active during our application process and flag that up before you proceed with your order.
Do DV or EV HTTPS certificates mean this is a good company?
No.
An audience member at EdgeConf noted that YTS.RE, a pirate torrent site, used to have an EV certificate. While the torrent site has since changed domains, this seems to check out: YTS.RE is a registered company in the UK and they have a postal address at a coworking space just near the Old St Roundabout.
Is YTS.re doing something illegal? Yes.
Does that change whether they're allowed to assert that they're definitely YTS.RE Ltd in their EV certificate? No.
SSL validation process concerns identity: this is an entirely separate matter from the ethics of a company. YTS.RE had a certificate because it's a real company, with an office just off the Old St Roundabout in London.
Who uses EV certificates?
Your bank, payments and cryptocurrency sites, eCommerce companies, tech companies like AirBnB, Twitter, GitHub, Microsoft and Apple.
Are there flaws in the EV process?
Undoubtedly. EV requires more validation than DV, but it's definitely possible. Improvements to how companies are validated for SSL will likely come as future additions to the EV Specification.
Are EV HTTPS certificates worth it?
Essentially the cost of EV is the cost of validation. As time goes on, and as there are more CAs, we suspect the competition will increase and the price of EV will go down.
However, the current per-year price of EV is less than a half a single day's work by an average programmer. The current basic per-month cost is a similar price to what companies often already pay for services like GitHub or Trello. This cost is manageable for most businesses.
What now?
If you've read all that and don't want identity markers, you can get an automatic domain validated certificate at no charge from Let's Encrypt or AWS Certificate Manager.
If you want to prove your companies real-world identity online, CertSimple provides high-assurance EV certificates simply and painlessly - we're the fastest in the world - meaning you can get a high-assurance certificate quickly and painlessly.