How to Block Clients with Application Logic (Cookies) on Heroku
Why Take This Approach
If you’re experiencing abuse within your application from users (defined as clients who are authorized by the presence of a cookie.)
You can leverage Expedited WAF to block users with defined cookies at the edge (firewall) network level completely blocking them from touching your application.
This leaks less information about your application to potential attackers, requires less application/dyno resources and helps prevent a variety of other attacks.
Conceptually, this works as if you’re “telling” the Expedited WAF Edge network to block any future request with the cookie you’ve named.
Prerequisites
What you need to get started:
- Expedited WAF add-on is setup in front of your application.
- You can identify bad behavior within your application.
- Ability to set cookies from within your framework
How To Block Clients by Cookie on Heroku
Set a cookie from within your application. This can be named anything you like (ex:
blocked-user)From your dashboard set the same cookie name (ex:
blocked-user) to be blocked
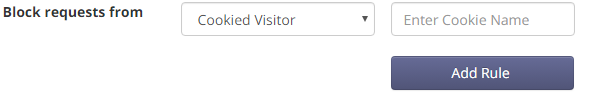
Every request to your application is filtered through the Expedited WAF edge network which automatically filters out any identifiable attacks. Adding a cookie blocking rule treats subsequent requests with that cookie as if they were attacks and blocks them.
Notes
- Only the name of the cookie is compared, not the value.
- You probably want to name the cookie something less obvious than
blocked-user. - Cookies are domain specific and will only be blocked/identfied from the domain they are set on, typically this is not a problem but if you’re using subdomains you may need to explicitly declare that the cookie is good across the root domain.
Framework resources
How to set cookies in different web application frameworks