
Who your browser trusts, and how to control it.
Don't want to trust Lenovo, Dell or the Chinese givernment? You don't have to.
July 12, 2021
First it was Superfish, then it was Dell's eDellRoot. In both cases, a root level SSL CA - whose private key is normally kept in an offline tamper resistent vault in an secured datacenter - was created with the private key available on desktop computers worldwide. Anyone could use that to impersonate any website they wanted to affected users.
So are there more? Probably. There's also CAs who don't properly handle their keys, like China's CNNIC. How do you know who you trust? And how do you control it?
The browser you're using right now trusts a bunch of certificate authorities. Which bunch of certificate authorities - properly called a 'root certificate store' - is determined by your OS and browser:
The major root certificate stores are Apple, Microsoft, Mozilla, and Android. When you visit a website, the website presents a certificate that's signed by another certificate, which is signed by another certificate, until you reach one of the certificates in the store you're using.
Each certificate store has its own requirements for a certificate authority to get added. However they all require certificate authorities to pass WebTrust for Certification Authorities, an audited assurance process for the policies and procedures for verifying identity, issuing certificates, handling keys, and more.
Occasionally CAs violate the WebTrust requirements: the Chinese government (CNNIC) and Symantec both recently issued fake certificates for google.com. In CNNIC's case, they gave their private key to a third party that issued the fake certificate. CNNIC was removed from the Android and Mozilla root stores, but the Microsoft root store - used by Chrome on Windows and Edge on Windows - only revoked the misissued certificates. Symantec's case was less severe: an accidental, but still troubling, misissuance: in this case the root stores kept their certificates and the employees responsible were fired.
Asides from Apple, Microsoft, Mozilla and Google's root store requirements and WebTrust, other efforts to ensure that CAs behave include certificate transparency, which we've discussed before.
But there's also you. If you're not sure whether ancient CAs or government authorities deserve your trust, you don't have to give it to them: more specifically, you can mark them as untrusted. This will make your browser show up a warning when you visit sites trusted by them.
Note: revoking a popular key will make your browsing experience somewhat awkward. However CNNIC and government CAs aren't part of your daily browsing experience, and you can enjoy the internet without trusting them.
Firefox on any OS
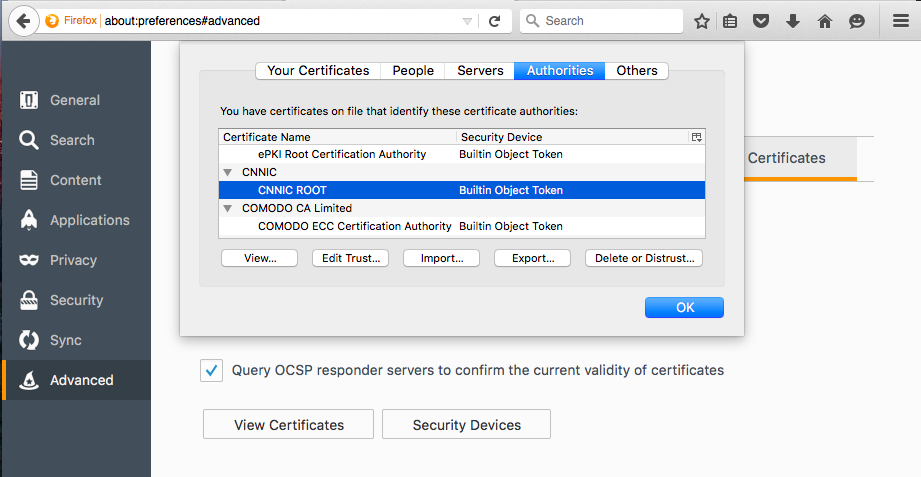
Firefox has quick, simple UI for marking a certificate as untrusted. Just open Firefox Preferences > Advanced > Certificates > View Certificates.
Select any certificate and click Delete or Distrust.
Edge or Chrome on Windows
If you're using Chrome or Edge on Windows, you'll be using the Windows certificate store. Windows downloads and installs root certificates as needed, but you can actually blacklist a certificate to stop it being installed later.
This is a cumbersome process, but works:
Fetch the certificates Windows would install
Get the full list of trusted root certificates Windows would install from Windows Update, and open it:
certutil -generateSSTFromWU rootcas.sst
invoke-item rootcas.sst
Windows Certificate Manager will show all the root certificates that Windows would auto install.
Export the certificate you don't want
- Right click the unwanted certificate, All tasks, Export
- Go through the steps picking the defaults
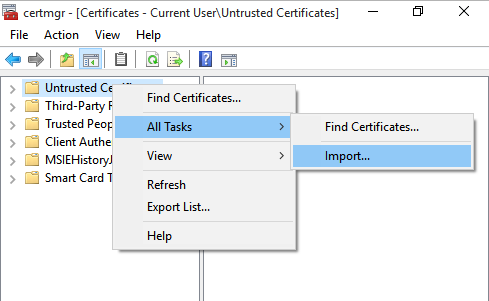
Import the certificate back into the 'Untrusted Certificates' group.
- Run
certmgr.mscand visit Untrusted Certificates > Certificates. - Right click Untrusted Certificates and pick All tasks - Import
You'll now see the certificate listed in the Untrusted Certificates.
Chrome, Safari and other browsers on OS X
OS X's inbuilt Keychain Access app is competent, similar to Mozilla's. They're also the only key management UI that put a search box in their UI.
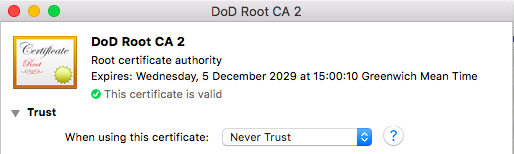
- Open Applications > Utilities > Keychain Access
- Under Category pick Certificates Click on the CA in question
- Expand Trust and for When using this certificate select Never Trust
Android
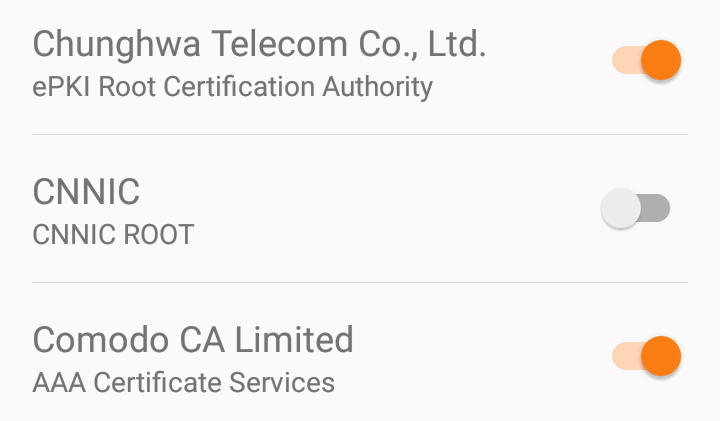
It's incredibly easy to disable roots you don't trust on Android.
In Settings, tap Security > Trusted credentials. Tap the certificate you'd like to remove, scroll down and touch Disable.
iOS
iOS seems to be the only device which doesn't allow removal or disabling of it's inbuilt root certificates. There's no way to remove or not trust a certificate included in Apple's root certificate store.
While Apple Configurator 2 allows you to create a Config Profile which can add certificates, and some WiFI providers use Config Profiles to install additional root certificates.
If you want to check for and remove added certificates:
- Open Settings > General.
- If any profiles are installed, you'll see Profiles & Device Management - it appears underneath 'VPN'. If it doesn't appear there are no active configuration profiles.
- Open Profiles & Device Management, and tap on a configuration profile to remove it.
